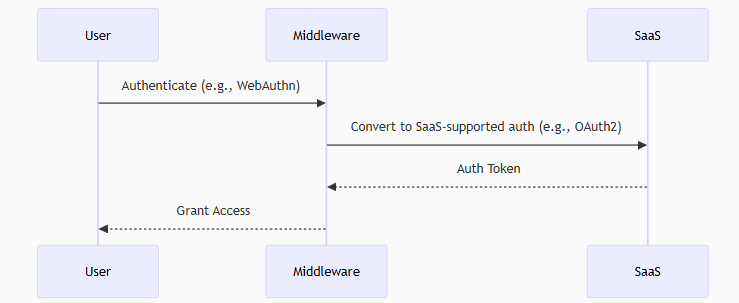
Let’s talk about something that’s both cool and slightly terrifying: using eBPF to watch socket syscalls before your fancy encryption kicks in. Yeah. You know that HTTPS request you were so proud of? The one that uses TLS and keeps your users “safe”? eBPF saw the plaintext before TLS even had a chance to clear its throat.
Wait, what?
At the syscall level — right at the edge of kernelspace — there’s a tiny window where everything your app says is still in cleartext. It hasn’t hit OpenSSL yet. It hasn’t been base64’d, hex’d, gzip’d, or otherwise obfuscated. It’s just sitting there, raw and readable.
That’s where this eBPF program jumps in with its metaphorical notebook and says, “Oooh, what’s this? Looks like a GET request to /secrets with a bearer token, neat.”
So what’s actually happening?
This program hooks into the connect, accept, read, write, etc. syscalls. When your app makes a socket connection and starts sending data, it snags the buffers. Literally — it reads the message you’re about to send, before any encryption, because you haven’t even handed it to the TLS library yet.
Want to fingerprint HTTP headers? Easy. Want to detect TLS handshakes? Sure — it even looks for ClientHello. Want to build a creepy little audit trail of who sent what where, with process info and directionality? Done.
Why does this matter?
Because most developers — and honestly, a lot of ops/security folks — think “I’m using HTTPS” is a full-stop safety guarantee.
But with kernel-level observability like this, HTTPS is a magician’s act that starts after the rabbit’s already out of the hat. The kernel saw the rabbit. The kernel can tell you the rabbit’s name, the address it was going to, and the hand that threw it.
So if you’re running sensitive apps (think login forms, auth tokens, secrets in HTTP headers — don’t lie, I’ve seen it), and you think encryption is a bulletproof cloak, just remember: anything you send before TLS gets its act together is up for grabs.
Is it useful? Absolutely.
Is it powerful? Wildly.
Should we maybe… pump the brakes on how much introspection we’re doing from inside the kernel? Yeah, probably.
Because the moment we say “sure, just parse app-layer data in-kernel,” we’re blurring the line between trusted computing base and trusted surveillance platform.
TL;DR
Encryption is great. But it starts after the syscall.
eBPF runs at the syscall.
So… yeah. Your secrets might be showing.